Expertos en ciberseguridad y tecnología
En Consultora Tecnológica, ofrecemos servicios de ciberseguridad, pentesting, análisis de seguridad, desarrollo de plataformas digitales personalizadas y manejo de tus bases de datos para garantizar velocidad, seguridad y escalabilidad


Servicios de Ciberseguridad
Ofrecemos pentesting, análisis de seguridad y desarrollo de plataformas digitales a medida.
Pentesting y Análisis


Evaluamos vulnerabilidades reales en tu infraestructura con pruebas de caja negra, gris y blanca.




Desarrollo a Medida
Diseñamos y optimizamos plataformas digitales garantizando velocidad, seguridad y escalabilidad en tus procesos.
Desarrollo de Base de Datos
Optimizamos tus bases de datos para garantizar un rendimiento rápido, seguro y escalable. Implementamos procesos de automatización para mejorar la eficiencia. Realizamos migraciones sin riesgos.
Proyectos Innovadores
Desarrollamos soluciones personalizadas en ciberseguridad y optimización digital.


Pruebas de Seguridad
Ofrecemos pentesting en diversos niveles para detectar vulnerabilidades reales en su infraestructura digital y garantizar la protección de sus aplicaciones y datos críticos ante amenazas informáticas.
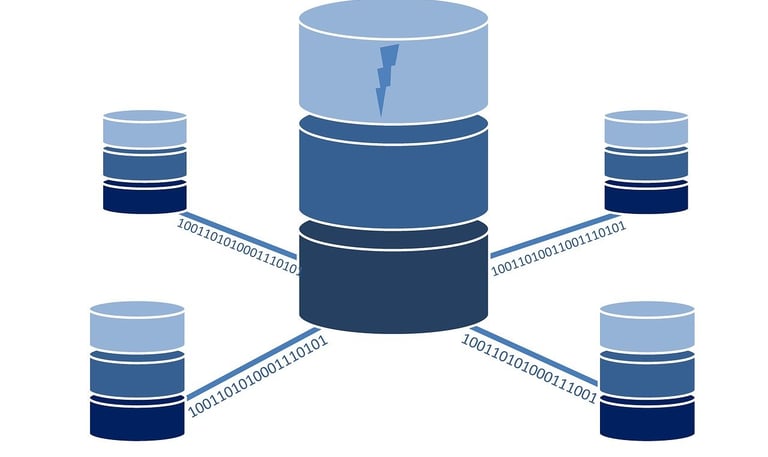
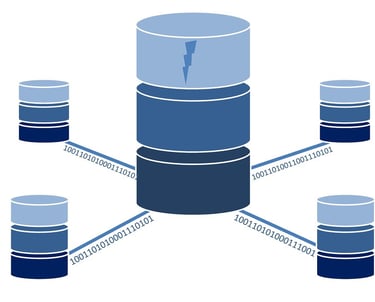
Bases de Datos
Mejoramos el rendimiento de tus bases de datos con automatización, optimización y migraciones seguras. Nuestras soluciones garantizan consultas rápidas, estructuras eficientes y una gestión confiable de la información.

Excelente servicio de pentesting, identificaron vulnerabilidades que no habíamos detectado antes. Muy recomendados.
Juan Pérez

La monitorización en tiempo real ha mejorado nuestra seguridad significativamente. Un equipo muy profesional y confiable.
María López

★★★★★
★★★★★
Seguridad
Protegemos tu infraestructura con ciberseguridad avanzada.
Desarrollo
Optimización
contacto@consultora-tecnologica.site
+52 449-469-69-44
© 2025. All rights reserved.